Questioning the Badge

This year at CES instead of the traditional badges with a barcode, we got fancy NFC enabled ones. I did some playing with it at the show, but didn’t really have the time to look to see what was actually encoded on it. With a better set of tools, and a bit more time, curiosity got the best of me so I wrote a quick app to dump and decode the content.
I don’t want to get too deep into how NFC works, but essentially the tag is like a really simple RFID powered memory card. When you swipe it with a reader it gets energized and gives up the content that was written to it. You can encode pretty much any data you want on the tag, and it’s up to the reader to understand what, if anything, to do with it. The most common use cases are to open a URL, send an SMS, or launch an app on the device.
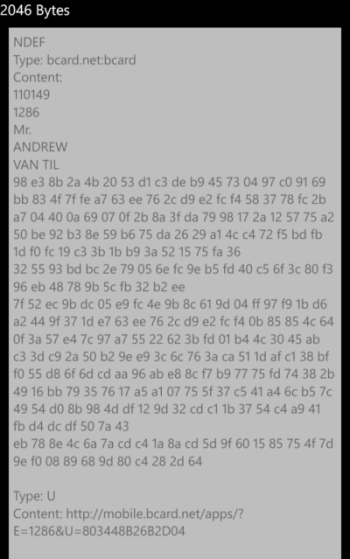
In this case, the tag actually contains two records. One (actually the second record on the tag) that contains a URL to a website that highlights the vendors that made/encoded the tag and points at the official CES app, the other is a bit more interesting because it is a custom NDEF record that is intended to work with a specialized application (probably this one). Taking a closer look at the payload of the record we can see that the front part is simple ASCII, with a couple numbers (probably an ID) and my name, but unfortunately the second part is some sort of binary blob that I haven’t been able to make sense of. Most likely it’s the full contact details (looking at the screenshots for the app), encoded in a way that only the app (or someone with more time than me) could unravel.
